FutureFeed Explorers Webinar Series: Mastering Configuration Items (CIs)

Maintaining baseline configurations for IT products isn’t just a best practice—it’s a necessity for security and compliance. In the ever-evolving landscape of cybersecurity, organizations must demonstrate not only that they have policies in place but that they enforce them effectively.
As part of the FutureFeed Explorers Webinar Series, the episode Mastering Configuration Items (CIs) explored how organizations can strengthen compliance by implementing well-documented technical configurations. Experts shared insights on how CIs bridge the gap between high-level policies and real-world enforcement, making assessments smoother.
Why Configuration Items Matter
Think of Configuration Items as the technical blueprints that validate your policies. While policies define what needs to be done (e.g., “All systems must disable unused ports”), CIs provide the how—detailing the specific technical settings and configurations required to achieve compliance.
For example:
- Policy: “All workstations must apply XYZ security settings.”
- Configuration Item (CI): A document or script detailing the specific group policies, registry settings, or system configurations that enforce the policy.
- Evidence: Screenshots or system reports demonstrating that the configuration has been applied.
Key Challenges in Configuration Management
Many organizations struggle with maintaining accurate configurations due to:
- Inconsistent documentation – Variations in recording configuration settings can lead to discrepancies during assessments.
- Outdated configurations – Failure to regularly update configurations increases security risks.
- Lack of standardization – Without a clear framework, different teams may adopt varying approaches, leading to confusion.
The webinar highlighted these pitfalls and provided strategies to mitigate them, ensuring that organizations maintain effective and reliable documentation.
How Configuration Items Strengthen Compliance
- Simplifying Assessments
During an assessment, Configuration Items serve as concrete evidence that your systems meet security baselines. They create a clear link between policies and the actual configurations applied, ensuring that organizations can prove they “walk the talk.” - Supporting Assessors
Assessors don’t just want to hear that an organization is compliant—they want to see it. CIs provide granular, actionable proof that security requirements are being met. By linking CIs to relevant Policies, Procedures, and Technology in FutureFeed, organizations can offer a complete, traceable picture of their compliance efforts. - Filling the Gap
Many organizations have security policies but struggle to prove that they have implemented them effectively. Configuration Items close that gap, acting as a bridge between governance and the tangible settings applied to IT systems.
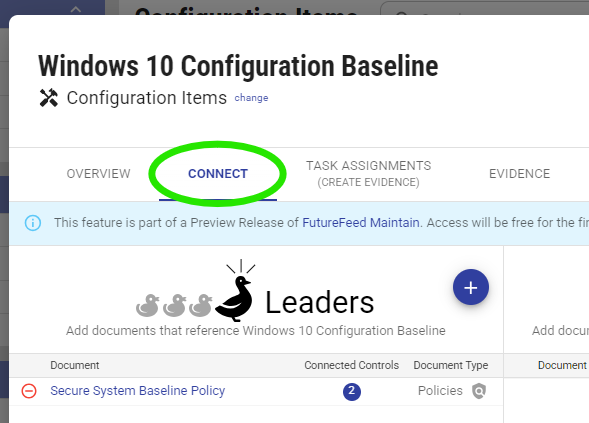
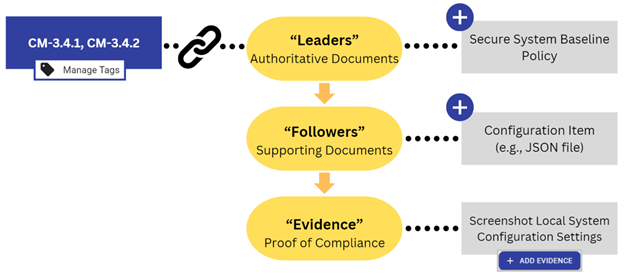
How to Use Configuration Items in FutureFeed
Configuration Items are now part of the Reference Documents category in FutureFeed, alongside Diagrams, Lists, and the Shared Responsibility Matrix (SRM).
- Link CIs to Compliance Elements:
Use the Connect Tab in FutureFeed to associate CIs with relevant Policies, Procedures, and Technology. This creates a cohesive compliance picture that’s easy to navigate and assess. - Organize Technical Baselines:
Upload and manage documents like JSON files, configuration guides, or scripts that define your IT product baselines. - Demonstrate Evidence:
Pair CIs with Evidence—such as screenshots or system reports—to show that configurations are actively applied and enforced. Upload this Evidence directly to FutureFeed for centralized tracking and easy access during assessments.
Example: Disabling Unsecure, Plain-Text Ports and Services
The Policy:
“All systems must disable unsecure, plain-text ports and services to mitigate the risk of data interception and unauthorized access.”
The Configuration Item:
A document outlining the specific steps required to implement this policy, such as:
- Unsecure Services Disabled: Replacing Telnet with SSH for remote management and ensuring plain-text protocols like FTP and HTTP are replaced with secure alternatives such as SFTP and HTTPS.
- Port Restrictions: A configuration file or script that disables unsecure ports like 21 (FTP), 23 (Telnet), 80 (HTTP), and 110 (POP3), while enforcing secure protocols like HTTPS (443) and SSH (22).
The Evidence
- A firewall configuration screenshot showing that unsecure ports are disabled.
- A vulnerability scanner report confirming no active plain-text services.
- A system command output (e.g., netstat) displaying only secure ports in use.
Why CIs Are More Important Than Ever
With growing emphasis on cybersecurity frameworks like NIST SP 800-171, organizations are under increased pressure to provide tangible proof of compliance. Policies alone aren’t enough—companies must show that they actively enforce their security baselines.
Configuration Items serve as the missing link, ensuring that organizations don’t just document security measures but also implement and maintain them. By integrating CIs into FutureFeed’s compliance management system, businesses can strengthen their security posture, streamline assessments, and improve their overall risk management.
Stay tuned for the next episode in the FutureFeed Explorers Webinar Series as we continue to explore best practices in compliance and cybersecurity.
