Best Practices for Achieving and Maintaining CMMC Compliance
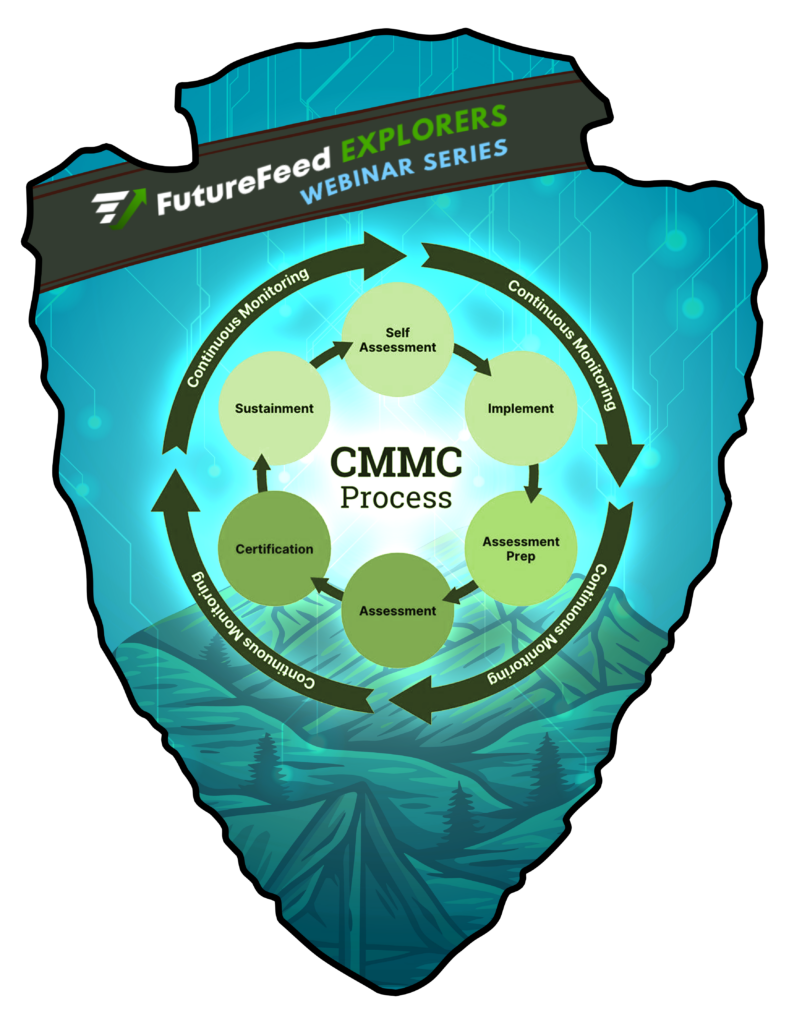
CMMC compliance isn’t just about passing an assessment — it’s about implementing security practices that protect your organization and the sensitive information with which you are entrusted long-term.
This webinar series will guide you through the entire CMMC journey, from initial preparation to certification and beyond, with expert insights, best practices, and real-world tips to make compliance manageable and sustainable.
FutureFeed Explorers goes beyond the “What”, explaining the “Why” behind each step of the CMMC journey. Understanding your destination is essential; “if you don’t know where you’re going you might up some place else”.
Topics:
- Establishing What’s in Scope – How to start on the right foot
- Addressing Non-Technical Controls – The role of policies and procedures
- Addressing Technical Controls – Understanding what’s behind the technobabble
- Selecting External Service Providers – Determining who is right for you
- Creating and Managing POA&Ms – Creating and executing a remediation plan
- Building and Curating Your Body of Evidence – Satisfying adequacy and sufficiency
- Managing the Certification Assessment – Being prepared and in control
- Responding to Change – Maintaining compliance in a dynamic environment
Upcoming Webinar

Why is Access Control so Darn Important for CMMC? Understanding the AC controls and how to address them
Wed. Feb. 25th at 1PM ET
Hosted by Stuart Itkin with John Nolan, VP of Compliance at ISI
This educational webinar explores why Access Control (AC) and Identity and Access Management (IAM) are so critical to CMMC compliance. We will examine how attackers commonly achieve unauthorized access, including misconfigured access controls, social engineering and deception, and improper physical access. The session will also explain what IAM is, why it remains one of the most challenging areas of cybersecurity, and the real-world consequences organizations face when IAM controls are weak or poorly implemented.
Register now.
Past Webinars
Shared Responsibility – CMMC in the Cloud | Featuring C3 Integrated Solutions
Tues. November 18th at 1PM ET
Hosted by Stuart Itkin and Amy Williams of FutureFeed, with Scott Whitehouse, VP of Compliance, C3 Integrated Solutions
For organizations pursuing CMMC certification, this reliance on the cloud introduces both opportunity and complexity.
While cloud service providers assume responsibility for satisfying certain NIST SP 800-171 control requirements—sometimes in whole, sometimes in part—understanding where their responsibility ends and yours begins is essential.
Watch the replay.
Be CMMC Assessment Ready, Not Just CMMC Compliant | Featuring Secure Centric
Thu. September 18th at 2PM ET
Hosted by Rachel Leidy and Stuart Itkin of FutureFeed, with DeLora Rosario, Chief and Resilience Officer, Secure Centric
Compliance on paper isn’t enough—you must be ready to prove it. Join FutureFeed and Secure-Centric to learn the difference between being CMMC compliant and truly assessment ready. Discover how to make your assessor’s job easier, avoid common mistakes, and lead your assessment with clarity and confidence so your organization can secure and retain DoD contracts.
Watch the replay.

Identifying and Responding to Change: Why Cybersecurity (and CMMC) Require Continuous Monitoring | Featuring ISI
Thu. July 31st at 1PM ET
Hosted by Rachel Leidy and Stuart Itkin of FutureFeed, with John Nolan, VP of Compliance at ISI
Explore why continuous monitoring is a critical requirement for both cybersecurity and CMMC conformance. Discover how everyday changes—like a new system, a vendor update, or employee turnover—can quietly expose your environment to risk.
Watch the replay.

Addressing CMMC’s Non-Technical Controls: The Role of Plans, Policies and Procedures | Featuring CompliancyIT
Wed. June 11th at 1PM ET
Hosted by Rachel Leidy and Stuart Itkin of FutureFeed, with Leia Shilobod, Founder of CompliancyIT
Policies and procedures define behavior, align your team, and prove to assessors that you’re in control—ensuring both non-technical and technical safeguards are applied consistently. Learn how to build CMMC-aligned documentation and kick off your compliance journey.
Watch the replay.

Managing Scope: Identifying and Limiting Your CUI Boundary | Featuring PEAK Complyance
Wed. April 16th at 1PM ET Hosted by Rachel Leidy and Stuart Itkin of FutureFeed, with Nancy Laney, President @ PEAK Complyance
Your journey to achieving CMMC compliance starts with scope: identifying, and in some cases reducing your CUI boundary. Getting scope right will limit the cost and time to achieve and maintain compliance. Getting it wrong can leave sensitive information exposed and your organization noncompliant.
This webinar will take you through the process of establishing and defining your CUI boundary and show you how to categorize and inventory both in scope and out-of-scope assets.
Download Whitepaper.
Watch the replay.
Mastering Configuration Items (CIs) | Featuring Peak InfoSec
Tues. January 29th at 1pm ET
Hosted by Rachel Leidy and Matthew Titcombe, CEO at Peak InfoSec
Read the blog and watch the replay highlights here.