Scoping: The First Step on Your CMMC Journey
Getting off on the right foot is essential
Embarking on the path to Cybersecurity Maturity Model Certification (CMMC) is a pivotal moment for any organization in the defense industrial base. Just like planning a cross–country road trip, your success depends on charting your route carefully—and for CMMC, that first milestone is scoping. Defining the precise boundary of what you must protect sets the tone for every step that follows, helping you avoid costly detours, unnecessary controls, and assessment delays.Embarking on the path to CybersecurityEmbarking on the path to Cybersecurity Maturity Model Certification (CMMC) is a significant step for any organization in the defense industrial base. But like any journey, success hinges on starting off on the right foot. For CMMC, that first step is scoping—and getting it right can make the difference between a streamlined certification process and one riddled with delays, gaps, and costly surprises.
In simple terms, scope defines the “box” that encloses everything that must be protected—your systems, people, processes, and locations that handle Controlled Unclassified Information (CUI) or Federal Contract Information (FCI). Getting this boundary right is essential because it identifies what will be assessed and where security controls must be applied. It requires understanding your environment deeply enough to confidently say what’s in and what’s out.

What Is Scoping and Why Does It Matter?
Scoping is foundational because it sets the parameters for everything that follows in your compliance effort. Your security controls, documentation, and assessments are all tied to this boundary. If your scope is too broad, you might end up applying expensive and unnecessary controls to systems that don’t need them. If it’s too narrow, you risk missing critical assets—something that can have serious consequences during a CMMC assessment.
Just as importantly, scope defines what assessors will evaluate. It determines which assets are subject to the NIST 800-171 requirements, what needs to be addressed in your System Security Plan (SSP), and where assessors will focus their time and scrutiny. Starting with a clear, well-reasoned scope ensures that both your security investments are effective and your assessments run smoothly.
Understanding and Categorizing Your Assets
A key part of scoping is identifying and categorizing your assets. This includes not just your IT systems, but also your people, your business processes, your physical locations, and any third-party providers involved in the handling of CUI or FCI. Categorization isn’t just a bureaucratic exercise; it’s the foundation for determining where security requirements need to be applied, what is required in security documentation, and how assets will be handled during assessments.
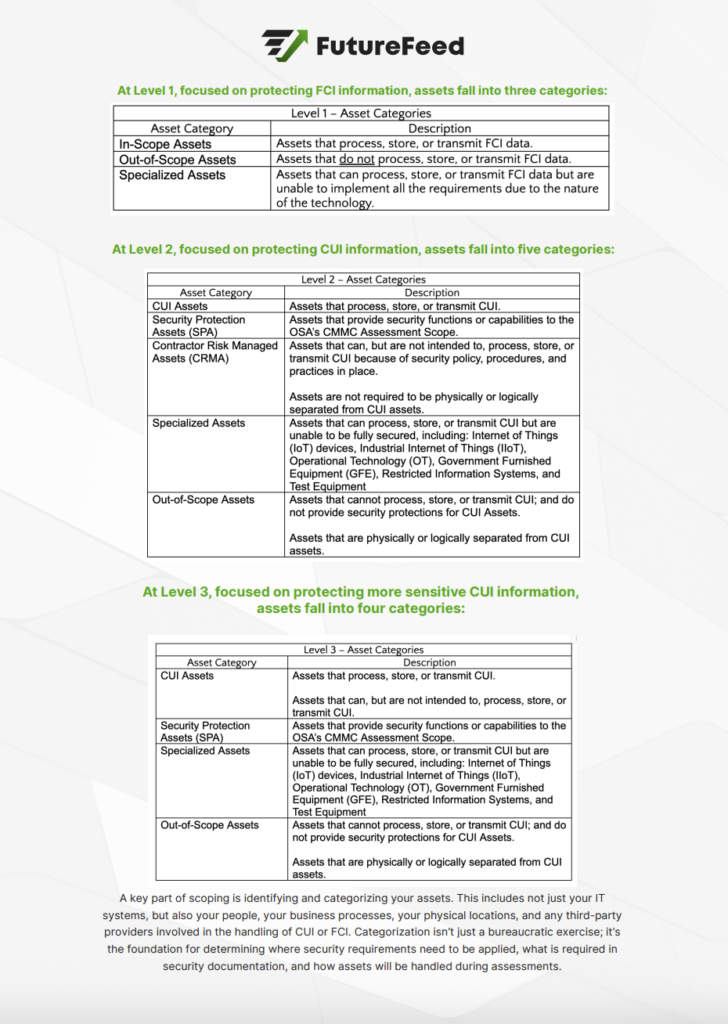
– At Level 1 (protecting FCI): assets fall into 3 categories
– At Level 2 (protecting CUI): assets fall into 5 categories
– At Level 3 (more sensitive CUI): assets fall into 4 categories
The Scoping Process: A Step-by-Step Approach
Establishing scope is a structured process. It begins by reviewing your federal contracts to identify where CUI or FCI are involved. This involves determining whether clauses like FAR 52.204-21 for FCI or DFARS 252.204-7012 for CUI appear in your contracts.
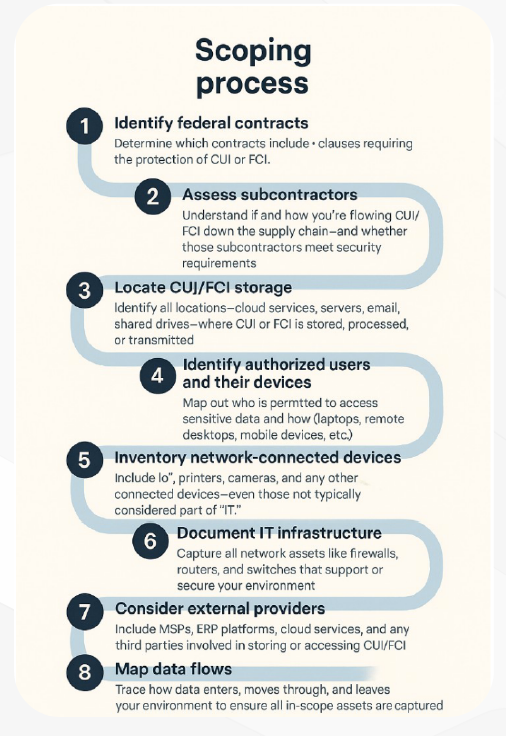
Next, determine whether you are sharing FCI or CUI with subcontractors. If you are, ensure that your agreements with these subcontractors include the appropriate contract clauses that specify their responsibility for protecting the FCI or CUI you share with them. This includes flowing down the necessary security requirements to guarantee they implement adequate safeguards in accordance with your compliance obligations.
After determining involved subcontractors or suppliers, map out where FCI and CUI are stored, processed, and transmitted internal to your organization; within your facilities, IT systems, and cloud environments.
This step involves more than just identifying servers—it also includes recognizing data locations across employee devices, cloud applications, and remote work setups.
Identify the users authorized to access FCI and CUI, along with the devices they use and their work locations (on-site, remote, or hybrid).
This mapping process may uncover unexpected risks, such as home printers, unmanaged mobile devices, or unauthorized cloud services being used to store or access CUI.
After cataloging your internal systems, shift your focus to external service providers. This includes managed service providers (MSPs), enterprise resource planning (ERP) vendors, cloud environments, and cloud applications.
- Inventory External Providers: Create a list of all external providers that support your organization, including those providing IT, cloud, or managed services
- Assess Data Interaction: For each provider, determine whether they store, process, or transmit FCI or CUI.
- Verify Compliance Requirements: For any provider that interacts with FCI or CUI, ensure they meet the applicable security requirements:
- FedRAMP Moderate: Required for cloud service providers handling CUI.
- CMMC Compliance: Required for providers subject to CMMC assessment and certification.
- Document Compliance Assurance: Ensure that your agreements with external providers include the appropriate security requirements and retain evidence of their compliance status.
The final step is to create a data flow map that visually traces how FCI and CUI move across your organization. This map should illustrate the flow of data between systems, departments, external providers, and any other relevant boundaries.
- Visualize Data Movement: Map the complete lifecycle of FCI and CUI, from creation to storage, processing, transmission, and disposal.
- Identify Critical Connections: Ensure that all connections where data is accessed, transmitted, or stored are accurately represented.
- Validate Scoping Accuracy: Use the data flow map to cross- check your scoping efforts, making sure no critical connections have been missed.

When and How Scope Can Be Reduced

In many organizations, particularly those that serve both commercial and government customers, it may be possible—and highly beneficial—to reduce scope. Doing so lowers the number of systems and users subject NIST SP 800-171 and CMMC, which in turn reduces the cost and effort involved in implementing and maintaining the security.
Scope can often be minimized through isolation, which means implementing logical or physical separation between systems, users, and data that need to store, process, transmit, or protect CUI and those that do not. Isolation reduces the number of assets, users, and locations that must meet security requirements, making compliance more manageable. Isolation can be achieved in several ways:
- 1. Logical Isolation: Logical isolation involves using technology and access controls to separate systems handling CUI from those that do not. This can include:
- Network segmentation: Using Virtual Local Area Networks (VLANs), subnets, or software-defined networking (SDN) to separate systems that process CUI from general business systems.
- Role-based access control (RBAC): Restricting access to CUI systems to only those users who require it based on their roles.
- Access Control Lists (ACLs) / Rule Sets: Enforcing strict rules that limit access to in-scope assets.
- Dedicated systems: SImplementing separate data storage systems, email accounts, or customer collaboration platforms for DoD-related work, ensuring that CUI is handled only within approved, isolated systems.
- 2. Physical Isolation: Physical isolation is the most direct form of separation, ensuring that systems processing CUI are physically separate from other systems. This may include:
- Dedicated facilities or spaces: Establishing a secure, separate area or building for systems and personnel handling CUI.
- Isolated enclaves: Creating dedicated rooms, labs, or data centers that are physically restricted to authorized personnel.
- Secure workstations: Placing systems that process CUI in a secure room with controlled physical access.
Isolation isn’t just a technical solution—it may require reengineering your business processes.
This involves rethinking how data is handled, who interacts with it, and how it flows across your organization. For example:
- Redesigned workflows: Adjust workflows so that only authorized users can access or transmit CUI, minimizing exposure.
- Distinct Documentation Systems: Maintain separate document management tools for DoD and commercial data to prevent unauthorized access to CUI.
By strategically applying these isolation techniques—logical, physical, business process, and IT support—you can significantly minimize your compliance scope. This allows you to focus your compliance efforts on only the areas where CUI truly exists.
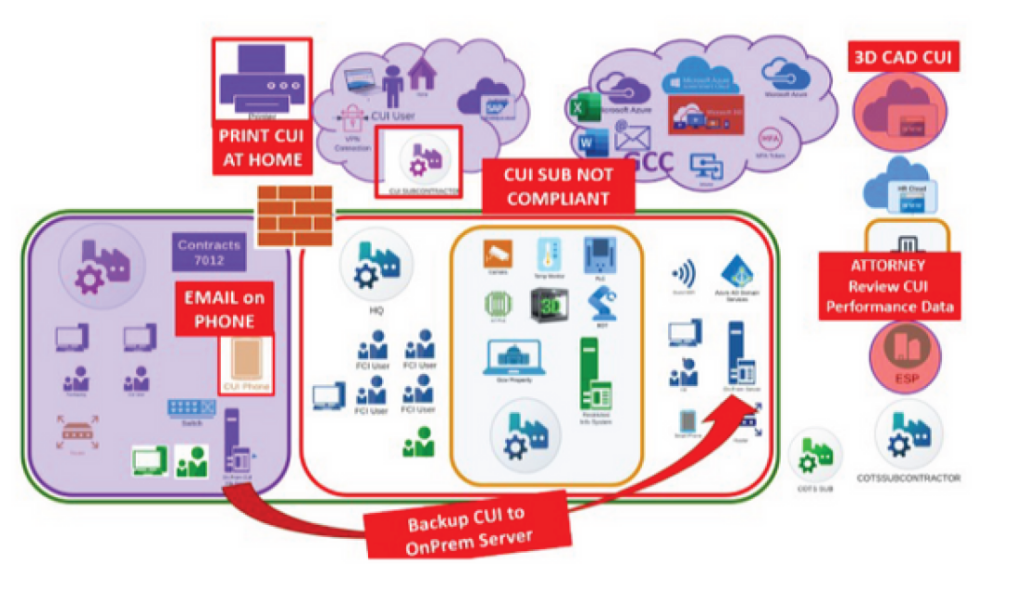
Common Mistakes That Undermine Scoping
Despite its importance, scoping is often misunderstood—or simply done incorrectly. One common mistake is overlooking assets that interact with CUI in non-obvious ways. A mobile phone used to check DOD-related emails, a home printer used by a remote worker, or a cloud application used by engineering staff can all bring unanticipated assets into scope.
Another frequent issue is poor flow-down to subcontractors. If you’re sending CUI to a supplier, partner, or subcontractor who isn’t properly secured, the risk
—and responsibility—falls on you. Even well-intentioned organizations can stumble here, especially when collaboration tools or shared access are used without the right controls in place.

The consequences of these mistakes can be severe. During an assessment, a single overlooked asset can lead to multiple control failures, forcing you to either halt the process or scramble to remediate.
Fixing these issues after the fact means reworking documentation, reassessing controls, and in some cases, redesigning your entire security architecture.
Understanding and Managing Your Assessed Scope: Avoiding Scope Drift

When your organization undergoes a CMMC assessment, the assessed and certified scope becomes the authorized environment to store, process, and transmit CUI data.
This scope is essentially a locked-in view of the systems, assets, users, and processes that were evaluated and certified during your assessment. It is crucial for your organization to maintain a clear and detailed understanding of this scope to prevent unintended scope changes that could impact your compliance status.
Monitoring and Planning for Scope Changes
Your organization must carefully monitor any planned changes to your environment, such as adding new systems, adopting new cloud services, expanding network segments, or modifying existing processes. Each of these changes has the potential to alter your assessed scope. If a change would bring new asset types or data flows into the scope of your CMMC certification, you may be required to undergo reassessment or recertification.
To avoid unintentional scope changes and maintain compliance:
- Establish a Scope Management Process: Document your assessed scope in detail, including which assets, systems, locations, and processes are included.
- Evaluate Changes Before Implementation: Implement a process where any planned changes to your environment are reviewed for their impact on your CMMC scope.
- Plan for Reassessment if Necessary: If a change is determined to expand or alter your scope, determine whether it can be postponed until your next recertification window. If not, prepare for a potential reassessment.
- Maintain Clear Documentation: Keep your System Security Plan (SSP), network diagrams, and asset inventory up to date with any changes that affect your scope.

The Bottom Line: Scoping Is Strategy

Ultimately, scoping isn’t just a technical task; it’s a strategic one. It defines the work ahead, shapes your compliance plan, and determines the efficiency of your CMMC journey. More importantly, it ensures that your organization is doing its part to protect the sensitive data it’s been entrusted with.
By starting off on the right foot and getting scoping right you set yourself up for success. You gain clarity, reduce risk, and avoid costly missteps. And in doing so, you take the first meaningful step toward becoming CMMC compliant—and toward securing the future of your business in the defense supply chain.
